Enterprise Risk Risk Assessments Controlling Risks Training Strategic Risk
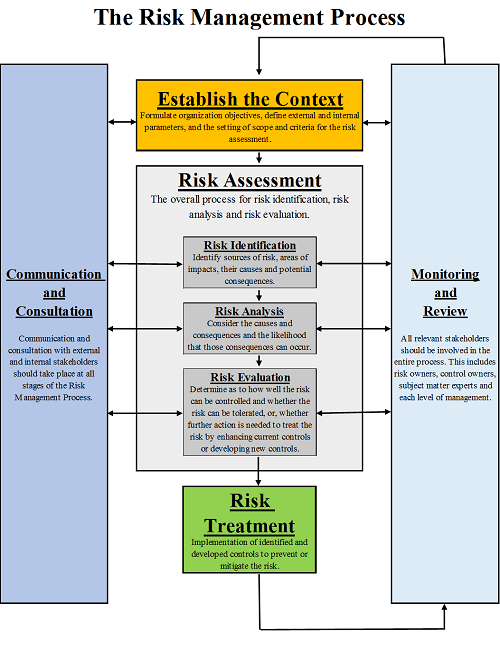
The risk process is a continuous process where an enterprise's risks are periodically reviewed, particularly with regard to the management or treatment of those risks through implemented controls. Although the process will vary according to the needs of an organization the process followed by NorthArm would follow the ISO 31000 process as summarized below, and adjusted according to the client's requirements.
Source: ISO 31000
Each phase of the risk management process is iterative, whereby there is continuous monitoring and review, as well as communication and consultation with the wider organization. A risk register resulting from risk assessments and reviews therefore would be a "living" document used in business decision making.
Assessing Risks
 Risks are assessed in a workshop environment where subject matter experts in each area or activity exposed or subject to or affected by an enterprise's risks participate in the assessment. Facilitation of the risk assessment is provided by NorthArm, such that there is a structured approach to formulating a risk profile.
Risks are assessed in a workshop environment where subject matter experts in each area or activity exposed or subject to or affected by an enterprise's risks participate in the assessment. Facilitation of the risk assessment is provided by NorthArm, such that there is a structured approach to formulating a risk profile. Risk Assessment Process
Establish the Context
An effective risk assessment commences with establishing the context, where the objectives of the activity are established (what are we trying to achieve), followed by the boundaries of the assessment (include only risks to the objectives). Any assumptions underlying the assessment should be noted. The date of the assessment as well as an attendance record should also be kept. All this information should be included in the risk assessment.
Risk Identification
Risk identification workshops with participants with knowledge and experience of the activity under review, designed and facilitated by a  risk specialist are the most effective way of identifying risks as:
risk specialist are the most effective way of identifying risks as: - the information obtained is directly relevant to the risk assessment;
- appropriate and structures processes are followed; and
- there is an effective use of time and the available expertise.
The workshop would reference all materials relevant to the risk assessment, including:
- previous events on site, at other sites in the organization, or within the industry locally, regionally and globally;
- previous events in other business contexts and environmental settings; and
- drawing on the judgement and previous industry experience of the subject matter experts.
A brainstorming worksheet would be used to record the risks, which then could be refined, sorted and entered into a risk assessment template for further analysis.
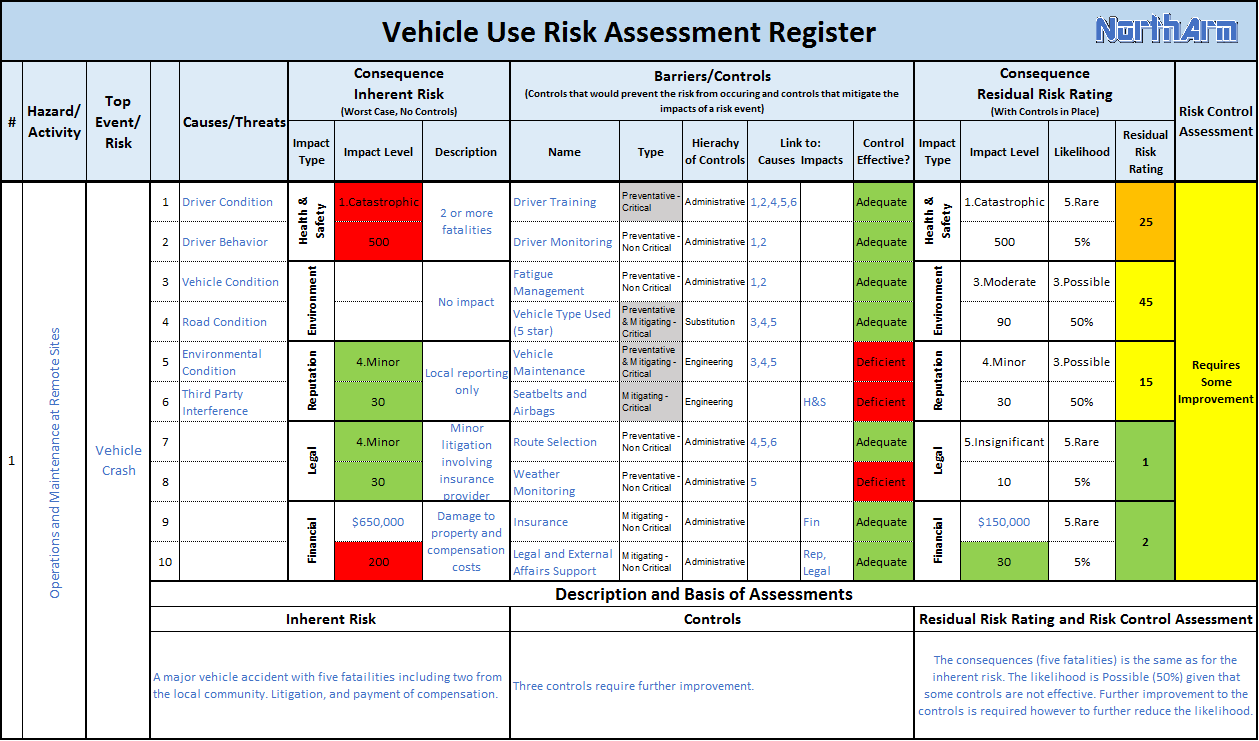
Each identified risk should include:
- the hazard (the activity or operation exposed to risk);
- the risk event or top event;
- causes or threats giving rise to the risk;
- the consequences in a worst case scenario (Inherent Risk) using the organization's risk matrix;
- preventative and mitigating controls or barriers; and
- a description of the risk including any plausible scenarios leading to the consequences.
Risk Analysis Once a risk has been identified, it is then further assessed and analyzed in terms of the magnitude of the causes or threats, the veracity of preventative controls or barriers to those causes or threats and how well the risk overall is controlled. Once the causes and preventative controls have been assessed, the probability of the risk being realized can be determined using likelihood tables and guidance.Inherent Risk
Once a risk has been identified, it is then further assessed and analyzed in terms of the magnitude of the causes or threats, the veracity of preventative controls or barriers to those causes or threats and how well the risk overall is controlled. Once the causes and preventative controls have been assessed, the probability of the risk being realized can be determined using likelihood tables and guidance.Inherent Risk
 The inherent risk is the plausible worst case scenario of the consequences. A number of consequence categories could be used to clarify the effects of the inherent risk .
The inherent risk is the plausible worst case scenario of the consequences. A number of consequence categories could be used to clarify the effects of the inherent risk .
These categories can include: - Health and Safety
- Health and safety impacts to employees and contractors;
- Environment
Impacts to land (surface and sub-surface), water, air and ecosystems;
- Reputation
- Impact on the enterprise's reputation including local and regional community reaction, news coverage, shareholder or stockholder reaction as well as governments and their agencies;
- Legal
Litigation impacts and regulatory action; and
- Financial
The financial cost to the enterprise
Likelihood What is the likelihood that a risk event will happen? A number of factors should be taken into account when considering likelihood;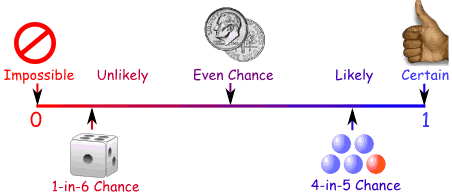
- What is the rate of occurrence of the risk event (in the industry and generally)?
- Has it happened at the organization before?
- How effective are the preventative controls?
- Each control or barrier should be assessed in terms of its effectiveness in preventing the risk.
- How well managed is the risk overall?
- Is it well controlled, or does it require further treatment (such as additional controls)?
With the above taken into account, a likelihood table can be used to estimate the likelihood of the risk event.
Consequences and Mitigating Controls or BarriersThe extent of the consequences should be assessed in terms of their impact, which may be the same as the inherent risk, or less. The impacts would be assessed for the same impact categories as for the  inherent risk as below:
inherent risk as below: - Health and Safety;
- Environment;
- Reputation;
- Legal; and
- Financial.
The level of impact of some categories may depend on the level of impact of others.How effective are the mitigating controls?- Each control or barrier to a consequence should be assessed in terms of its effectiveness in mitigating the risk.
- How well managed is the risk overall?
- Is it well controlled, or does it require further treatment (such as additional controls)?
A risk matrix is used to quantify the level of impacts of consequences.
Residual Risk
 The residual risk is a measure of the of the risk taking into account the controls or barriers in place. It is a product of the Likelihood and the impact.
The residual risk is a measure of the of the risk taking into account the controls or barriers in place. It is a product of the Likelihood and the impact.
The Risk Register records all aspects of a risk assessment and should contain the following elements:- Context of the risk assessment and why it is being completed;
- It should also include the scope, any reference materials and all participants;
- Organization objectives and expected outcomes of the proposed activity should also be recorded;
- Risks to the objectives and outcomes are identified;
- Each risk would be shown in detail including all causes, controls inherent risk and residual risk rating;
- Show how well the risk is managed and controlled
An example of the assessment part of a risk register is shown below.
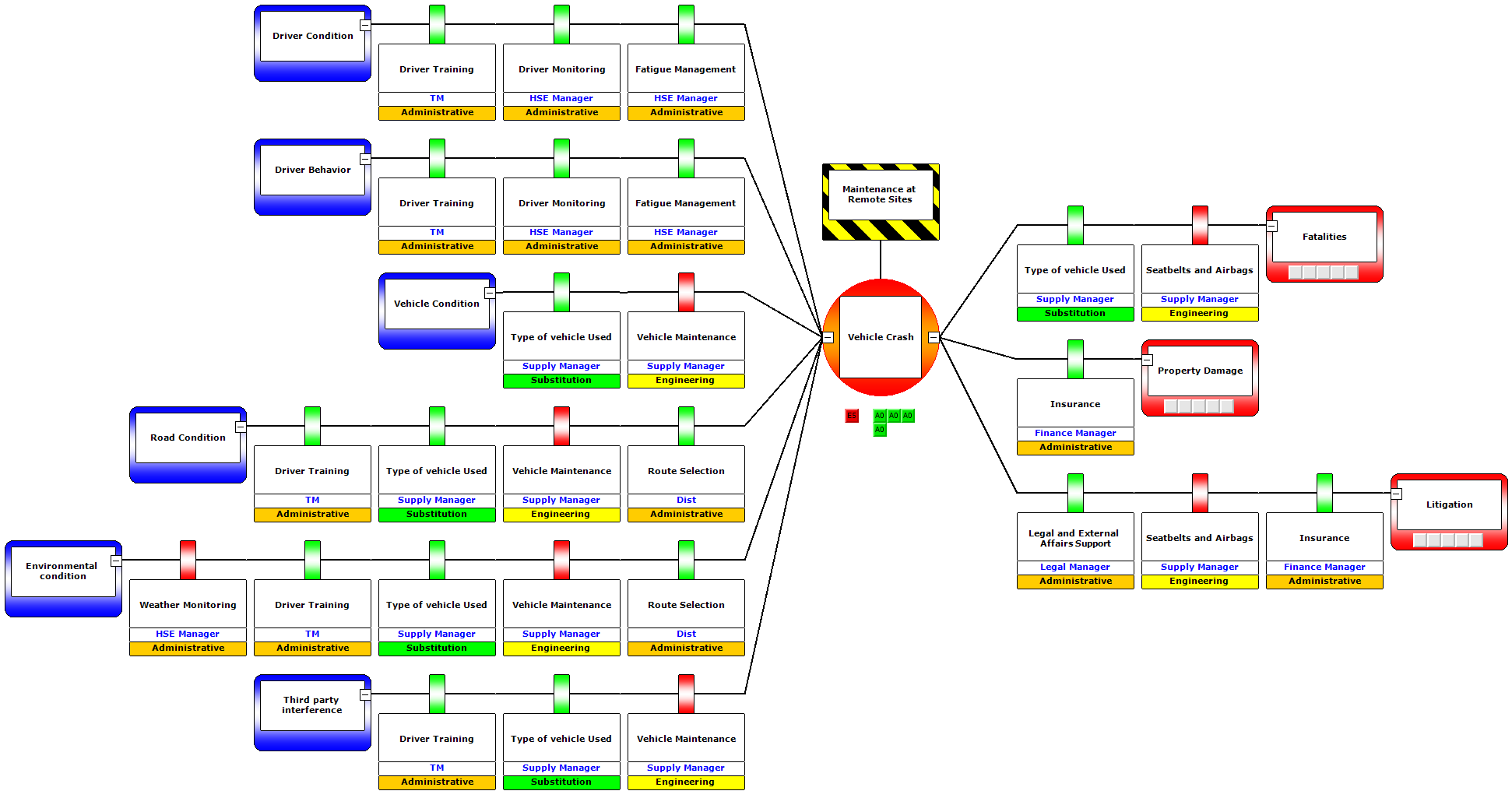
Use of Bow Ties in Risk Analysis
A bow tie is a diagrammatical representation of the risk. It shows each of the causes, all controls that are a barrier to each respective cause, the risk event and the consequences, as well as controls that act as barriers to each respective consequence. This allows for an effective analysis of the risk.
Risk Profile
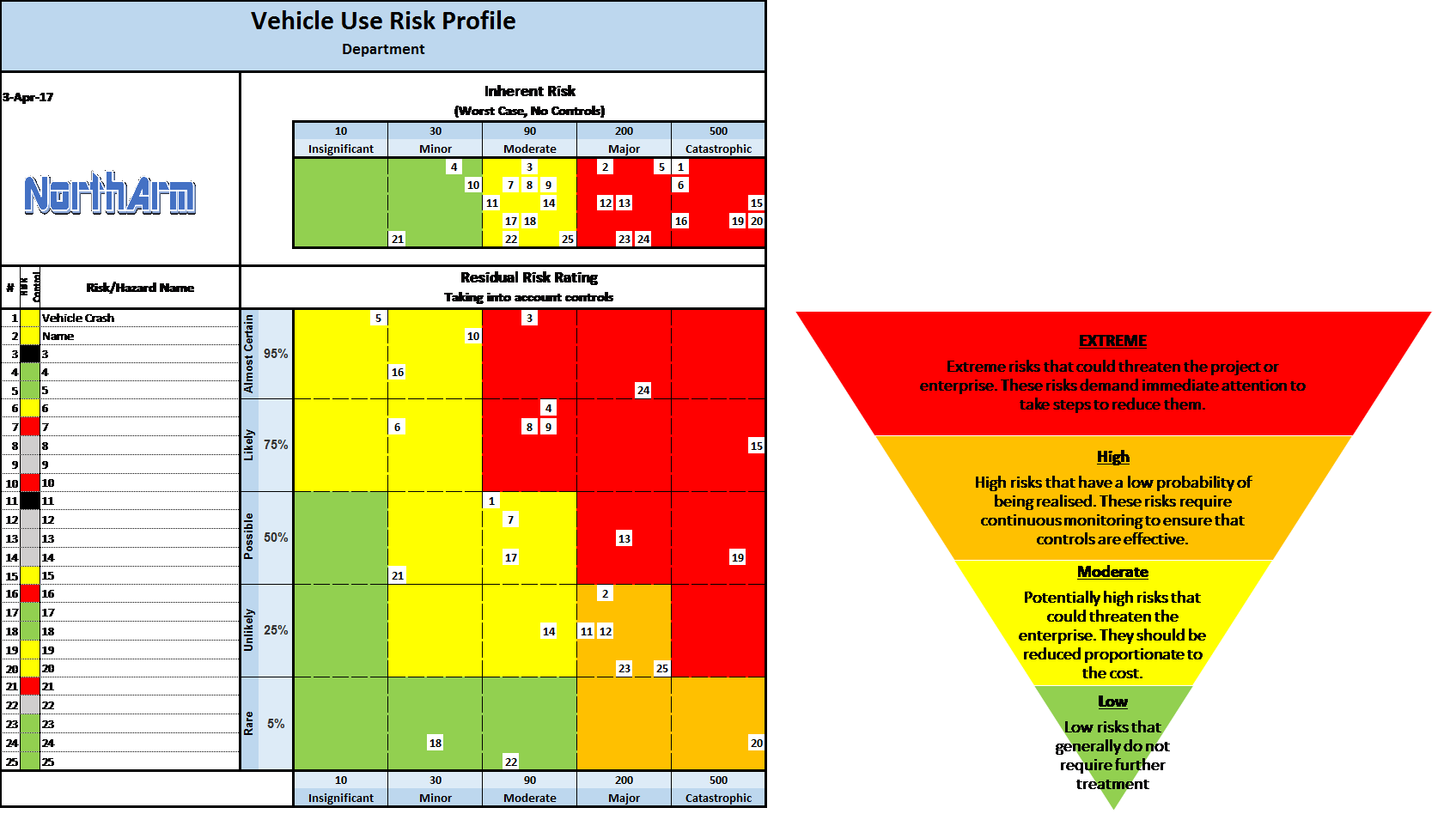
Once the risk assessment has been completed, a risk profile can be drawn showing all the risks in one diagram. The risks are shown in terms of their Inherent Risk (no controls) and the Residual Risk.
The Inherent Risk profile shows all the risks in a worst case scenario.
The risks are categorized in three groups; Minor, Moderate and Major/Catastrophic.
Residual risk are shown in terms of their severity in the risk matrix.
The risks are categorized in four risk level groups; Low, Moderate, High and Extreme. Depending on the level of risk identified, action may be required to reduce the risk.

 risk specialist are the most effective way of identifying risks as:
risk specialist are the most effective way of identifying risks as:
 The inherent risk is the plausible worst case scenario of the consequences. A number of consequence categories could be used to clarify the effects of the inherent risk .
The inherent risk is the plausible worst case scenario of the consequences. A number of consequence categories could be used to clarify the effects of the inherent risk .
 inherent risk as below:
inherent risk as below: